Feedly Threat Intelligence + ThreatConnect: Enhance context in your TIP
Combine Feedly’s AI-driven insights with ThreatConnect’s powerful TIP capabilities to accelerate analysis and improve response

15-Second summary
Feedly’s integration with ThreatConnect simplifies and enhances threat intelligence workflows by delivering relevant, contextual intelligence directly into your TIP, enabling deeper enrichment, smarter prioritization, and alignment with intelligence requirements — all with seamless health monitoring through our no-code service app.
With this no-code integration, you can:
- Enrich your investigations with high-signal intelligence from Feedly AI Feeds and Boards.
- Ingest IoCs, CVEs, TTPs, threat actors, and malware data with context into ThreatConnect.
- Correlate Feedly and ThreatConnect data to improve threat prioritization and response.
Boost your threat research with enriched, actionable insights from Feedly and ThreatConnect.
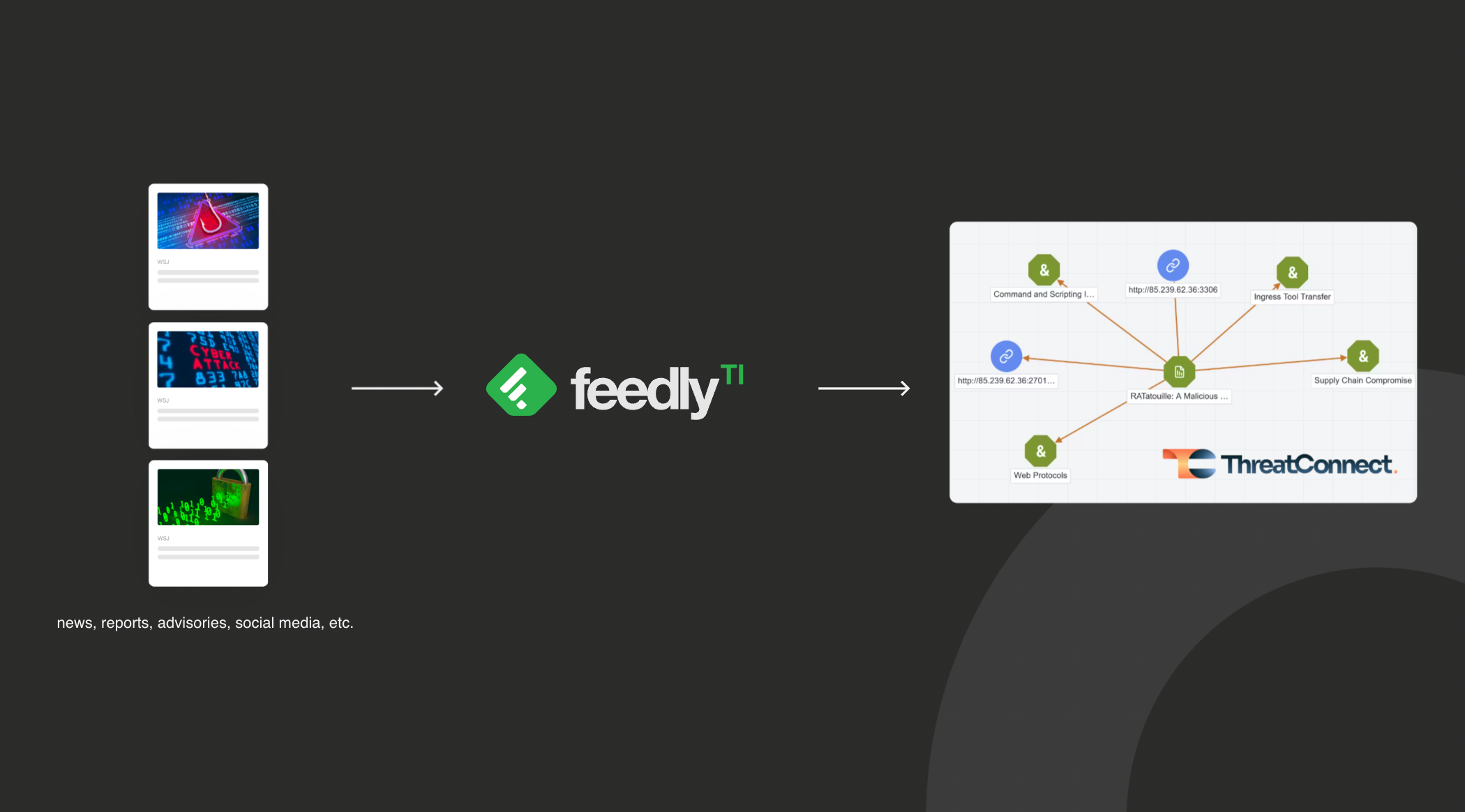
Enrich your investigations with high-signal intelligence
Many threat intelligence platforms struggle with the quality of their open-source data. Analysts often face a flood of low-signal content, such as irrelevant or duplicative articles, indicators that lack context, or vulnerabilities unrelated to their tech stack. This noise not only slows investigations but risks burying the few pieces of truly actionable intelligence.
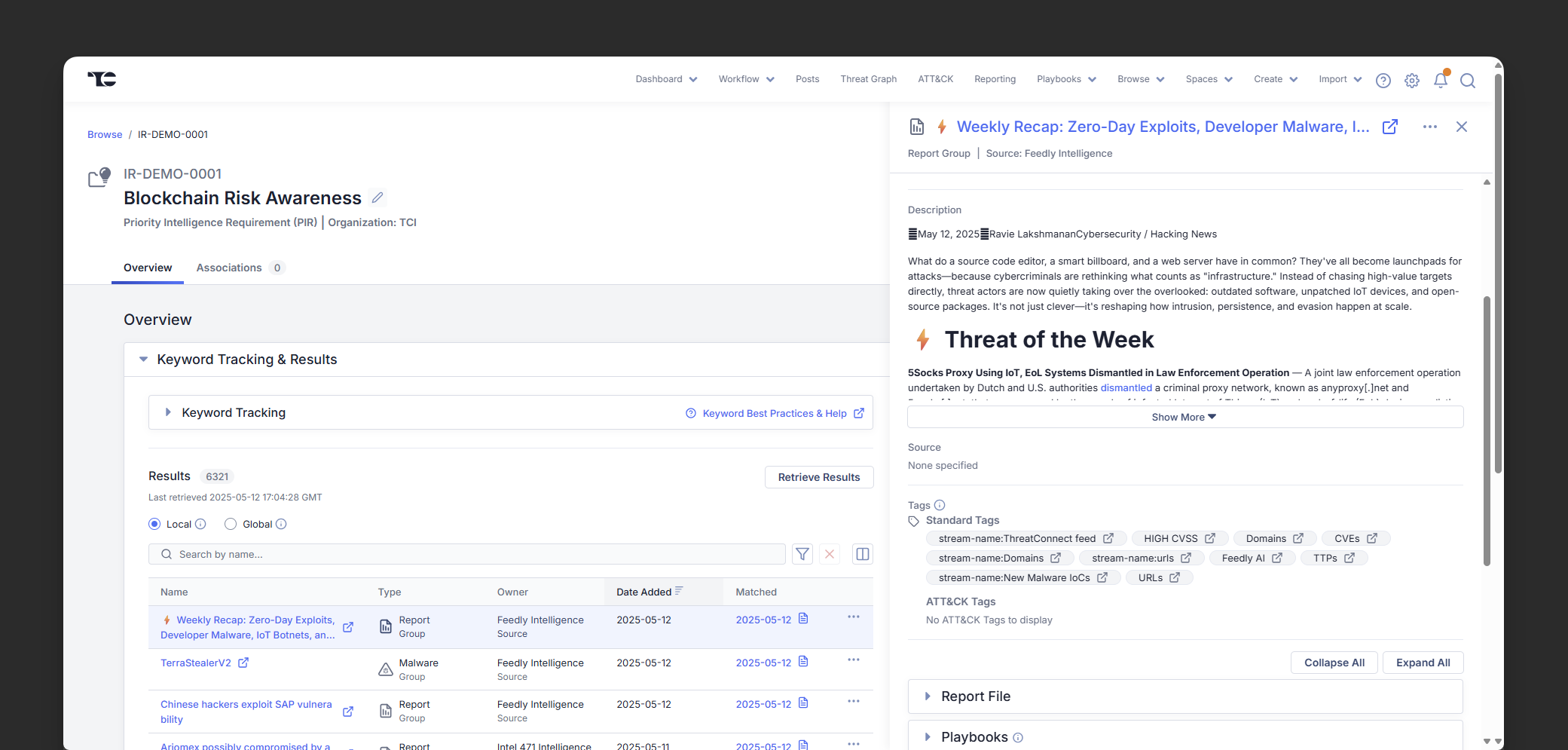
Feedly’s AI Feeds surface only the most relevant, high-confidence open-source intelligence from thousands of sources, filtering out noise and highlighting critical IoCs, TTPs, CVEs, malware families, and threat actors. This intelligence flows directly into ThreatConnect TI Ops as structured reports and indicators, with relationships and context preserved. Analysts can quickly enrich investigations with high-signal intelligence that integrates seamlessly with existing threat data.
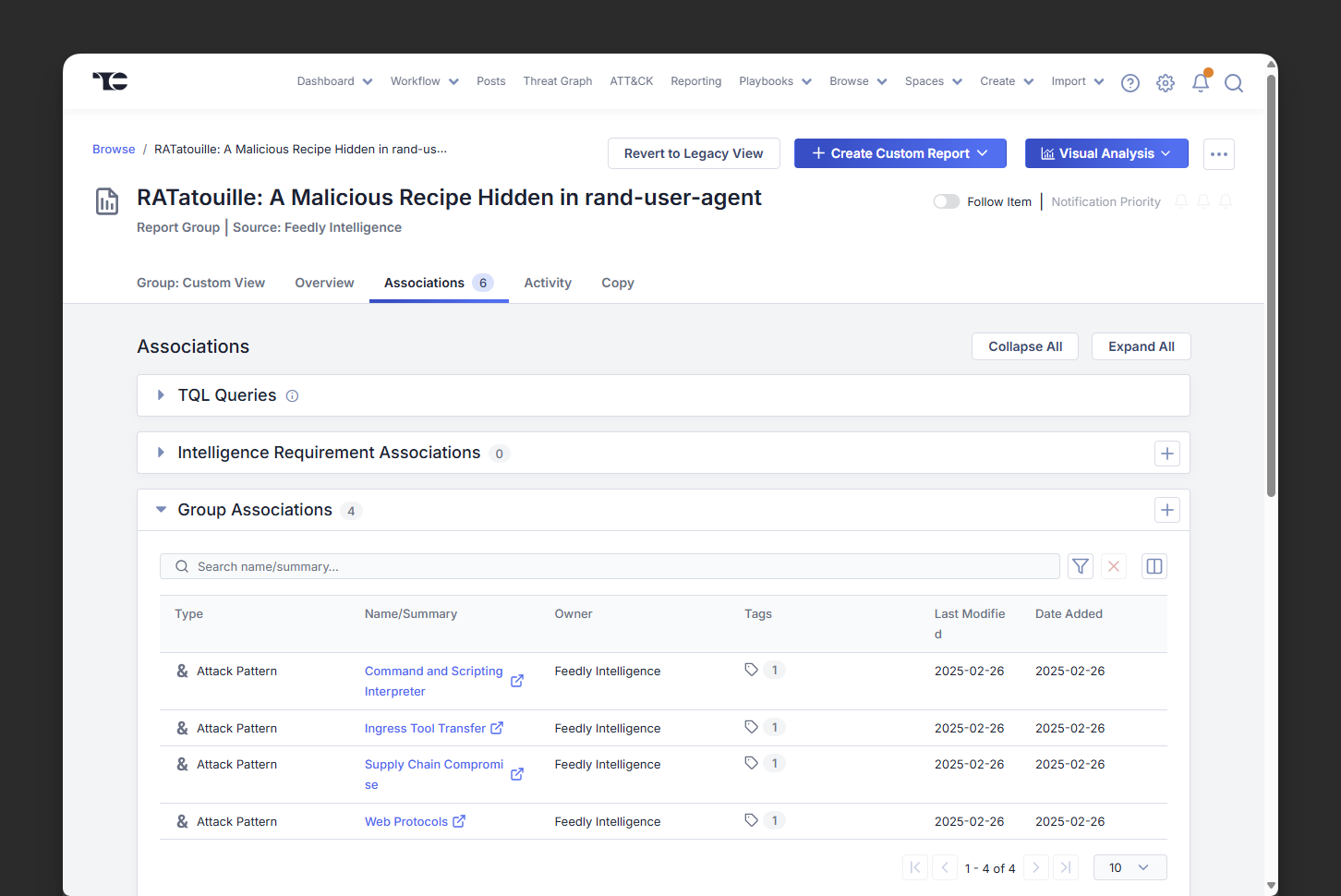
Ingest IoCs, CVEs, TTPs, threat actors, and malware data with context into ThreatConnect
Feedly AI automatically extracts and correlates key threat intelligence entities, such as CVEs, IoCs, TTPs, malware families, and threat actor names, from thousands of cybersecurity sources. Each article is processed into structured STIX 2.1 JSON and enriched with contextual relationships through the Feedly Threat Graph. This ensures that when intelligence is ingested into ThreatConnect, it arrives in a usable, standardized format that maintains the context necessary for effective analysis.
When Feedly identifies a relevant article containing actionable intelligence, it can automatically generate a report in ThreatConnect, complete with extracted indicators, TTPs, vulnerabilities, and linked threat actors or malware. This automation streamlines the intelligence ingestion process, reduces manual entry, and preserves the connections between entities, enabling CTI analysts to quickly pivot from high-level reporting to technical details during investigations.
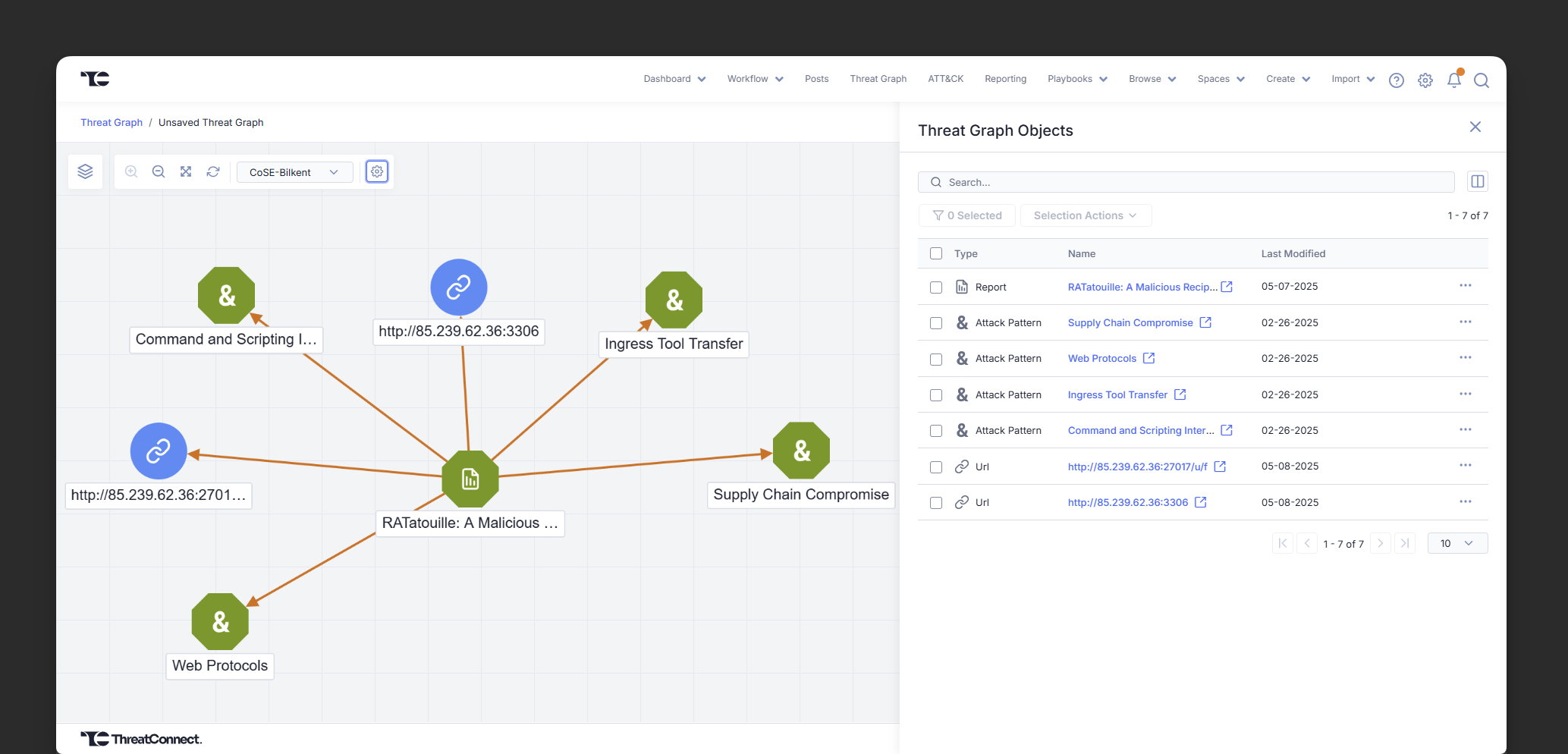
Correlate Feedly and ThreatConnect data to improve threat prioritization and response
Once Feedly intelligence is inside ThreatConnect, it becomes part of a larger, connected threat landscape that includes additional intelligence feeds, internal telemetry, and detection systems. Using the ThreatConnect Threat Graph, analysts can correlate Feedly-sourced indicators, TTPs, CVEs, and actor profiles with internal data to reveal deeper relationships and surface hidden threats.
This correlation improves both prioritization and response. Analysts can identify whether a Feedly-sourced IoC appears in internal logs, map emerging vulnerabilities to affected assets, or connect new TTPs to known adversary behavior. By linking external insights with internal visibility, teams can make better-informed decisions and act faster against the most relevant threats.
Intelligence from Feedly can be automatically mapped to ThreatConnect Intelligence Requirements, ensuring fidelity and relevancy with your most critical intel needs.
Conclusion
The integration of Feedly Threat Intelligence with ThreatConnect brings automation, precision, and context to your threat intelligence workflows. It eliminates the burden of low-signal open-source data and helps analysts move efficiently from ingestion to investigation to action. With structured, contextual intelligence flowing directly into your TIP, your team can stay focused on what matters: identifying threats early, prioritizing confidently, and responding with speed.
Try Feedly’s ThreatConnect integration
Simplify and enhance threat intelligence workflows by delivering relevant, contextual intelligence directly into your TIP.